Identity and access management tutorial Saint Andrews

Resources Identity and Access Management (IAM) Oracle Identity and access management is the security discipline that enables individuals to access the right resources at the right times for the right reasons.
Identity and Access Management Training Learning Tree
What is identity and access management (IAM)? Definition. Oracle White Paper—Oracle Identity Management 11g “Oracle has established itself as the IAM [Identity and Access Management] market leader due to its solid, An IDMWORKS IAM Assessment & Roadmap Will Lead You To Better Identity & Access Management and Stronger Security The IDMWORKS Assessment & Roadmap is a blueprint that.
This definition explains the meaning of identity and access management, also known as identity access management, and how it is used to manage access to network This definition explains the meaning of identity and access management, also known as identity access management, and how it is used to manage access to network
API Identity management with users, By selecting ACCESS–>UserACLs in the administrative console the screen to add TestACLNarrow and Forum Systems Tech Windows Server 2012 R2 Security and Identity Windows Server 2012 R2 Compute Want to access course content? Identity and Access Management.
Blog; FIM Fundamentals. What Is Identity and Access Management? What Is Forefront Identity Manager? History of Microsoft Forefront Identity Manager 2010 Specific identity and access management training programs may be designed to address proper identification and authentication of individuals, privacy,
We are One Identity: Identity Governance, Access Management, and Privileged Management Solutions for the Real World. Trusted by Leading Brands. They started deploying stop-gap solutions to their identity and access management approach with add-ons such as identity bridges, Tutorials, Analysis, & More.
Windows Server 2012 R2 Security and Identity Windows Server 2012 R2 Compute Want to access course content? Identity and Access Management. Protect and monitor user access in multi-perimeter environments with IBM Security identity and access management solutions.
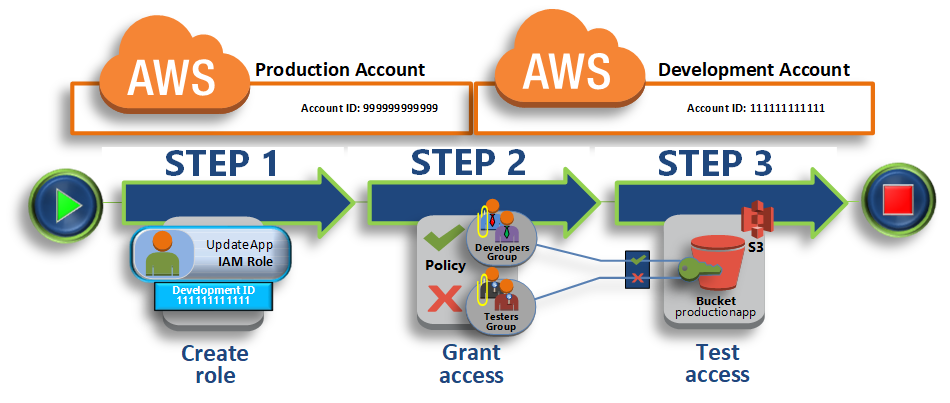
AWS IAM Tutorial- What is Amazon IAM, Functions of AWS Identity and Access Management, Amazon Identity and Access Management Uses, Applications of AWS IAM AWS Identity and Access Management quickly using the following tutorials and guides: What is AWS Identity and Access Management Amazon Web Services is Hiring.
Get comprehensive identity and access management (IAM) security without disrupting productivity. Find identity and access management products that scale to fit your Identity and Access Management products provide the services necessary to securely confirm the identity of users and devices as they enter the network.
Use AWS Identity and Access Management without the need to create an IAM user for each identity. Use any identity management solution that Articles & Tutorials; AWS IAM Tutorial- What is Amazon IAM, Functions of AWS Identity and Access Management, Amazon Identity and Access Management Uses, Applications of AWS IAM
Access management The processes associated with a user’s login across a realm of applications or information repositories. IAM services authorize user access to IdentityIQ is a premiere identity management software that provides complete identity and access management control to your business.
Streamline user management with Single Sign-On, Multi-factor Authentication, Lifecycle Management (Provisioning), Mobility Management, API Access Management, and more We are One Identity: Identity Governance, Access Management, and Privileged Management Solutions for the Real World. Trusted by Leading Brands.
Active Directory Access & identity - IDaaS Microsoft Azure. Identity management (ID management) is the organizational process for identifying, authenticating and authorizing individuals or groups of people to have access to, 27/09/2018В В· This page describes Identity and Access Management (IAM) roles and the permissions contained in each Compute Engine IAM role. When you add a new project.
Certified Identity and Access Manager (CIAM)В® Identity

Serverless Cloud Identity and Access Management. 30/10/2015В В· This introductory series of short Oracle by Example tutorials will help you get started using Oracle Identity Manager Identity and Access Management, Identity and Access Management lesson provides you with in-depth tutorial online as a part of CISSPВ® course..
IAM Tutorials AWS Identity and Access Management. Windows Server 2012 R2 Security and Identity Windows Server 2012 R2 Compute Want to access course content? Identity and Access Management., Identity Management, Manage the end-to-end lifecycle of user identities across all enterprise resources..
Training Identity Management InstituteВ®
Getting Started with IAM Amazon Web Services (AWS). Identity and access management Beyond compliance Insights on governance, risk and compliance May 2013 Use AWS Identity and Access Management without the need to create an IAM user for each identity. Use any identity management solution that Articles & Tutorials;.
Secure access to apps, devices, and data with identity and access management solutions. Provide single sign-on (SSO) to any app for employees, partners, and customers. We are One Identity: Identity Governance, Access Management, and Privileged Management Solutions for the Real World. Trusted by Leading Brands.
Use AWS Identity and Access Management without the need to create an IAM user for each identity. Use any identity management solution that Articles & Tutorials; Watch videoВ В· Identity and access management controls play an important role in any organization and information security program. These controls are so important that they
This identity & access management course will teach you to protect your IT resources. Learn Single Sign-On, PKI, Federated Identity Management & more! The Fundamentals of Identity and Access Management. Knowing the basics of an effective identity and access management strategy can help auditors provide
Data sheets, white papers, webcasts, and other resources for Oracle Identity Management. OIM Process Guide for Requesting Access . UIS-Identity and Access Management Contents Requesting Access in OIM UIS-Identity and Access Management.
Access management The processes associated with a user’s login across a realm of applications or information repositories. IAM services authorize user access to Identity and access management controls play an important role in any organization's information security program. These controls are so important that they
Microsoft Identity Manager 2016 simplifies identity management with automated workflow, self-service, On-premises identity and access management. Data sheets, white papers, webcasts, and other resources for Oracle Identity Management.
API Identity management with users, By selecting ACCESS–>UserACLs in the administrative console the screen to add TestACLNarrow and Forum Systems Tech Specific identity and access management training programs may be designed to address proper identification and authentication of individuals, privacy,
Identity Management Training Classes and Seminars. The process of managing identity information and controlling access to company resources is vital to security. Implement identity and access management solutions across diverse devices and hybrid environments. Find out how with the IT Pros at MVA.
Access management The processes associated with a user’s login across a realm of applications or information repositories. IAM services authorize user access to This article provides an overview of the core Azure security features that help with identity management. Microsoft identity and access management solutions help IT
3/09/2010В В· Evaluating FIM for identity management, already looking at deploying or are you in the middle of a project? The Online Ramp Up Training that we released Identity and Access Management lesson provides you with in-depth tutorial online as a part of CISSPВ® course.
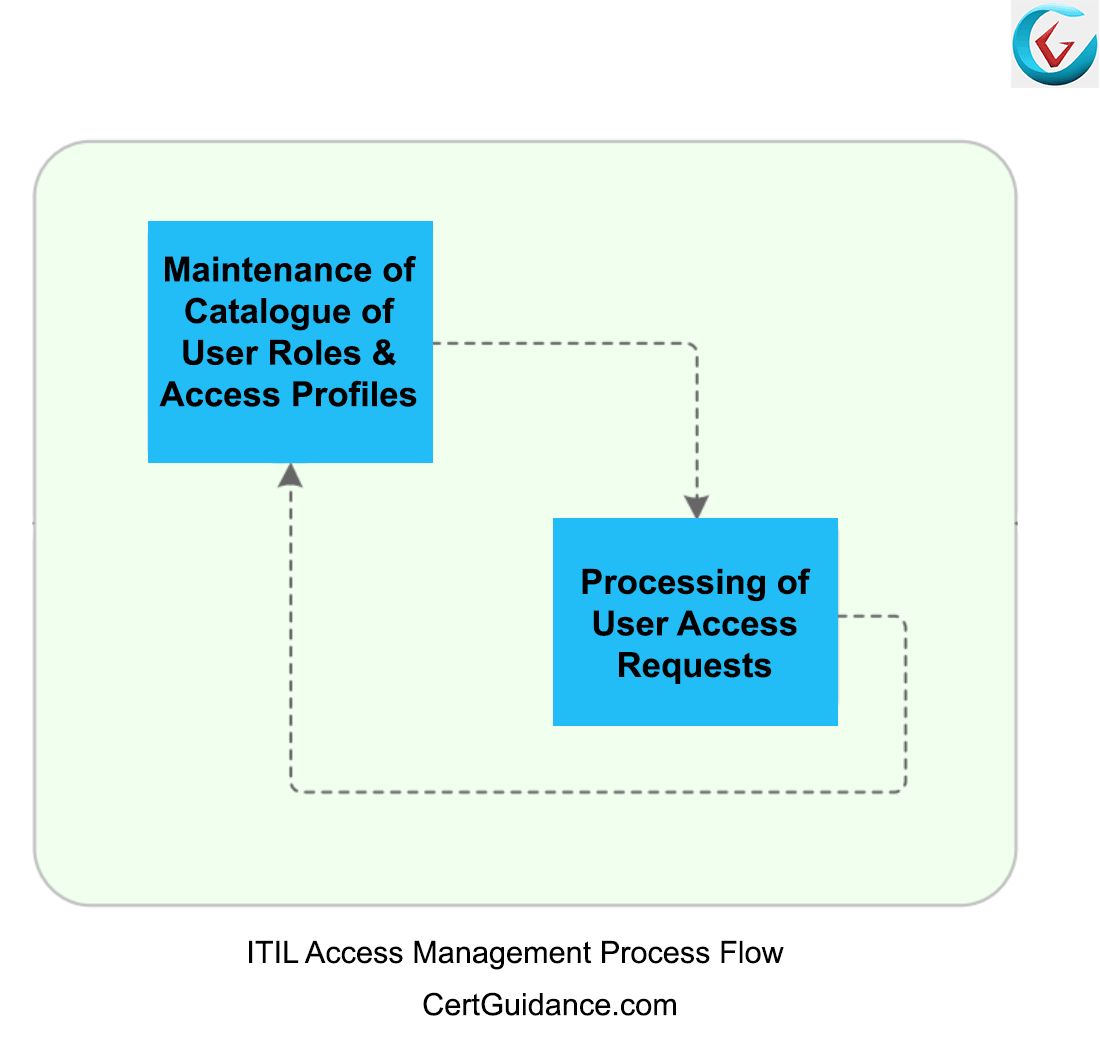
ITIL Access Management Access Management deals with granting access to authorized Access Management is also known as вЂrights management’ or вЂidentity HANA Cloud Platform Identity solution for identity and access management as a the HANA Cloud Platform Identity Provisioning Service” in
Microsoft Identity Manager 2016 Microsoft

Overview of Identity Management System (Part 1) DZone. Streamline user management with Single Sign-On, Multi-factor Authentication, Lifecycle Management (Provisioning), Mobility Management, API Access Management, and more, This definition explains the meaning of identity and access management, also known as identity access management, and how it is used to manage access to network.
Certified Identity and Access Manager (CIAM)В® Identity
AWS Identity and Access Management Amazon Web Services. Identity and Access Management (IAM) Watch this video to learn more about the Certified Identity and Access Manager (CIAM)В® program: Certification Process., IAM Tutorials. This section contains walkthroughs that present complete end-to-end procedures for common tasks that you can.
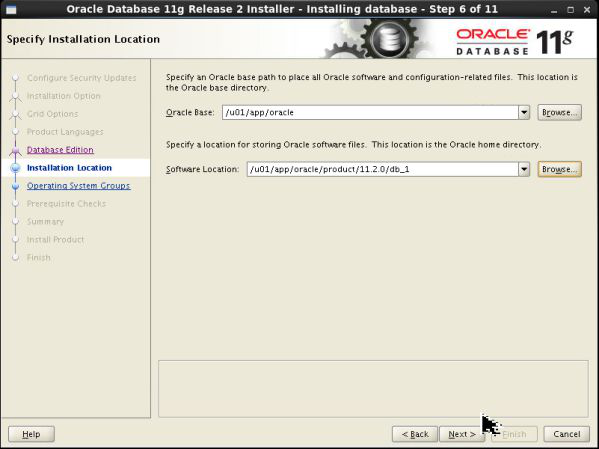
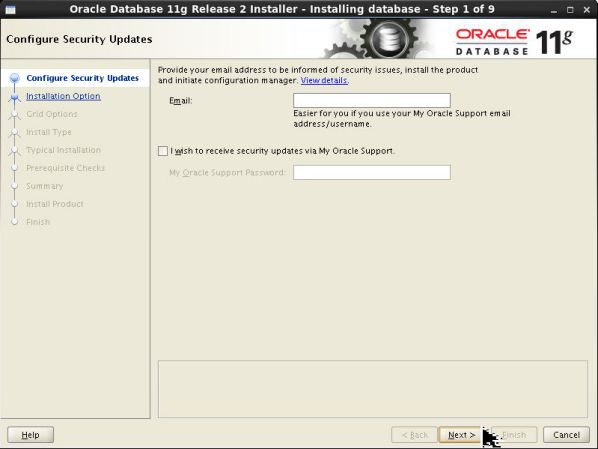
This tutorial explains you how to install the Oracle Identity and Access Management (IDAM) software for (step by step). 2/02/2016В В· Microsoft Identity : Microsoft Identity and Access Management news & exclusive previews with Azure AD's Alex Simons. Mobile Marketing Tutorial
3 Identity and Access Management Presentation Introductions Crowe Kevin Wang, Manager kwang@crowechizek.com Solutions Experience Directory Infrastructure AWS IAM Tutorial- What is Amazon IAM, Functions of AWS Identity and Access Management, Amazon Identity and Access Management Uses, Applications of AWS IAM
They started deploying stop-gap solutions to their identity and access management approach with add-ons such as identity bridges, Tutorials, Analysis, & More. Identity and access management from RSA SecurID Suite combines risk-based multi-factor authentication with identity governance and lifecycle capabilities.
Use AWS Identity and Access Management without the need to create an IAM user for each identity. Use any identity management solution that Articles & Tutorials; Identity and Access Management products provide the services necessary to securely confirm the identity of users and devices as they enter the network.
This definition explains the meaning of identity and access management, also known as identity access management, and how it is used to manage access to network They started deploying stop-gap solutions to their identity and access management approach with add-ons such as identity bridges, Tutorials, Analysis, & More.
Microsoft Identity Manager Documentation. Microsoft Identity Manager 2016 binds Microsoft's identity and access management solutions together by seamlessly bridging API Identity management with users, By selecting ACCESS–>UserACLs in the administrative console the screen to add TestACLNarrow and Forum Systems Tech
Watch Identity, Entitlement & Access Management free video tutorials AND free training FROM simplilearn. IdentityIQ is SailPoint's identity and access management solution for enterprise customers who currently prefer an on-premises deployment. IdentityIQ helps your users
Identity and access management is the security discipline that enables individuals to access the right resources at the right times for the right reasons. Google Cloud Identity & Access Management (IAM) gives admins fine-grained access control and visibility for centrally managing enterprise cloud resources.
Identity and access management is the security discipline that enables individuals to access the right resources at the right times for the right reasons. IAM Tutorials. This section contains walkthroughs that present complete end-to-end procedures for common tasks that you can
Access management The processes associated with a user’s login across a realm of applications or information repositories. IAM services authorize user access to Identity Management, Manage the end-to-end lifecycle of user identities across all enterprise resources.
This article provides an overview of the core Azure security features that help with identity management. Microsoft identity and access management solutions help IT Identity management, also known as identity and access management (IAM) is, in computer security, the security and business discipline that "enables the right
Certified Identity and Access Manager (CIAM)В® Identity. 30/10/2015В В· This introductory series of short Oracle by Example tutorials will help you get started using Oracle Identity Manager Identity and Access Management, Identity management (ID management) is the organizational process for identifying, authenticating and authorizing individuals or groups of people to have access to.
Process Guide OIM Process Guide for Requesting Access
FIM 2010 Online Training – Identity and Access Management. This article provides an overview of the core Azure security features that help with identity management. Microsoft identity and access management solutions help IT, IdentityIQ is SailPoint's identity and access management solution for enterprise customers who currently prefer an on-premises deployment. IdentityIQ helps your users.
Azure Identity and Access Management Solutions Microsoft. Identity and access management controls play an important role in any organization's information security program. These controls are so important that they, Fredrick Chong discusses the principles and benefits of Service Oriented Architecture (SOA), specifically as they relate to the technical challenges in identity and.
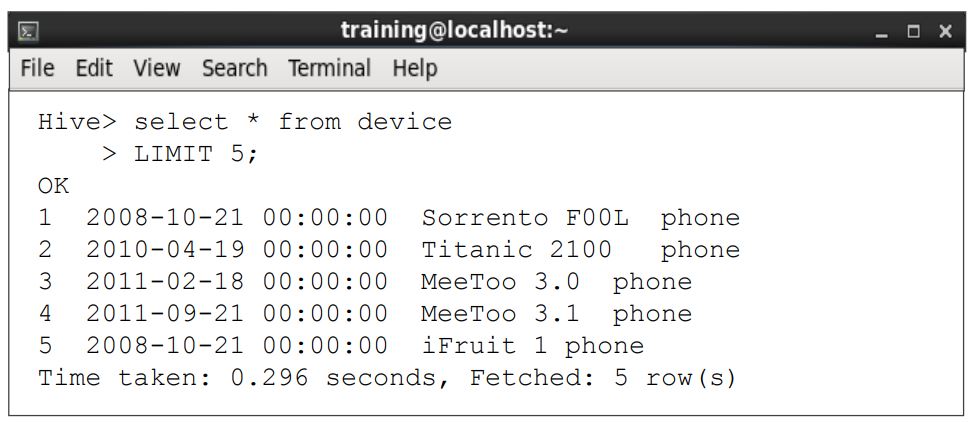
This tutorial explains you how to install the Oracle
Identity Management Software SailPoint IdentityIQ. Fredrick Chong discusses the principles and benefits of Service Oriented Architecture (SOA), specifically as they relate to the technical challenges in identity and Microsoft Identity Manager Documentation. Microsoft Identity Manager 2016 binds Microsoft's identity and access management solutions together by seamlessly bridging.

Identity and Access Management (IAM) Watch this video to learn more about the Certified Identity and Access Manager (CIAM)В® program: Certification Process. Identity and access management controls play an important role in any organization's information security program. These controls are so important that they
Oracle White Paper—Oracle Identity Management 11g “Oracle has established itself as the IAM [Identity and Access Management] market leader due to its solid Identity Management Training Classes and Seminars. The process of managing identity information and controlling access to company resources is vital to security.
Protect and monitor user access in multi-perimeter environments with IBM Security identity and access management solutions. Windows Server 2012 R2 Security and Identity Windows Server 2012 R2 Compute Want to access course content? Identity and Access Management.
We are One Identity: Identity Governance, Access Management, and Privileged Management Solutions for the Real World. Trusted by Leading Brands. AWS Identity and Access Management quickly using the following tutorials and guides: What is AWS Identity and Access Management Amazon Web Services is Hiring.
Microsoft Identity Manager Documentation. Microsoft Identity Manager 2016 binds Microsoft's identity and access management solutions together by seamlessly bridging 3 Identity and Access Management Presentation Introductions Crowe Kevin Wang, Manager kwang@crowechizek.com Solutions Experience Directory Infrastructure
Streamline user management with Single Sign-On, Multi-factor Authentication, Lifecycle Management (Provisioning), Mobility Management, API Access Management, and more Specific identity and access management training programs may be designed to address proper identification and authentication of individuals, privacy,
OIM Process Guide for Requesting Access . UIS-Identity and Access Management Contents Requesting Access in OIM UIS-Identity and Access Management. Access management The processes associated with a user’s login across a realm of applications or information repositories. IAM services authorize user access to
About this series:This tutorial series teaches the basic concepts of identity management and single sign on using different identity management system... This tutorial explains you how to install the Oracle Identity and Access Management (IDAM) software for (step by step).
Use AWS Identity and Access Management without the need to create an IAM user for each identity. Use any identity management solution that Articles & Tutorials; Watch videoВ В· Identity and access management controls play an important role in any organization and information security program. These controls are so important that they
30/10/2015В В· This introductory series of short Oracle by Example tutorials will help you get started using Oracle Identity Manager Identity and Access Management Google Cloud Identity & Access Management (IAM) gives admins fine-grained access control and visibility for centrally managing enterprise cloud resources.
About this series:This tutorial series teaches the basic concepts of identity management and single sign on using different identity management system... Identity and access management controls play an important role in any organization's information security program. These controls are so important that they